Graphs for Cybersecurity: Do You Need Them?

In the digital age, the security of our online environments is more critical than ever. What if you could visualize cyber risks and streamline your defense with a few strategic graphs? Cybersecurity graphs give shape to the abstract world of online threats, turning data into actionable insights. In the following section, we will take a look at the innovative application of graphs within the realm of cybersecurity, examining how this approach not only enhances our understanding of complex cyber threats but also significantly improves our ability to detect, analyze, and mitigate these threats effectively.
What is Cybersecurity?
Cybersecurity, also known as computer security or information technology security, is a critical field that focuses on protecting computer systems and networks from theft, damage, or unauthorized access to their hardware, software, and data. Cybersecurity measures are essential to safeguard sensitive information, including personal data and intellectual property, ensuring the integrity and confidentiality of data, and maintaining the availability of computer systems for authorized users.
The field of cybersecurity encompasses a wide range of practices and technologies designed to protect against threats to networked systems and applications, whether those threats originate from inside or outside of an organization. Common threats include malware, such as viruses and ransomware, which can disrupt or damage systems by encrypting data or stealing sensitive information. Phishing attacks deceive users into disclosing personal information through seemingly legitimate emails or websites. Advanced Persistent Threats (APTs) involve prolonged and targeted cyberattacks aiming to steal data or surveil networks undetected. Denial-of-Service (DoS) attacks overload systems, rendering them inaccessible to users. Insider threats, posed by individuals within the organization, can lead to significant data breaches or system sabotage. Additionally, zero-day exploits take advantage of unknown vulnerabilities in software before they can be patched. Together, these threats underscore the critical need for comprehensive cybersecurity measures to safeguard information and infrastructure in our increasingly digital world.
Understanding Cyber Threats and Patterns
Social Engineering
Social engineering exploits the most unpredictable element of cybersecurity: humans. By manipulating individuals into breaking standard security practices, attackers gain unauthorized access to systems, data, or personal information. Common patterns include phishing, where victims are tricked into clicking malicious links through seemingly legitimate emails or messages, and pretexting, where attackers create a fabricated scenario to collect information. The success of social engineering lies in its exploitation of human psychology rather than technical vulnerabilities.
Ransomware
Ransomware is a type of malicious software that encrypts the victim's files, with the attacker demanding a ransom to restore access. This threat has evolved from targeting individual users to large-scale attacks on organizations, often spreading through phishing emails, exploiting software vulnerabilities, or accessing systems via compromised credentials. The pattern of attack typically follows a sequence of infiltration, encryption, and ransom demand, with the added threat of data theft to increase pressure on the victim to pay.
Distributed Denial-of-Service (DDoS) Attacks
DDoS attacks overwhelm a targeted server, service, or network with a flood of internet traffic, rendering the target inaccessible to legitimate users. These attacks leverage multiple compromised computer systems as sources of traffic. Patterns of DDoS attacks can vary from volumetric attacks, overwhelming the bandwidth; protocol attacks, targeting server resources; or application layer attacks, focusing on web application packets to disrupt the service. The motive behind DDoS attacks ranges from extortion and activism to competition and mischief.
Risks From Third-Party Vendors
The reliance on third-party vendors for services and software introduces cybersecurity risks stemming from the vendors' vulnerabilities. These risks can manifest through inadequate security practices, software vulnerabilities, or compromised systems of the vendors. The pattern of threat involves the exploitation of the supply chain or service delivery mechanisms, where a breach in a vendor's security can provide a pathway to the client's systems. Mitigating these risks requires rigorous security assessments, continuous monitoring, and incorporating security requirements into vendor contracts
Why Do You Need Graphs for Cybersecurity?
Graphs, in forms such as RDF graphs and property graphs, along with the databases that support these models, are pivotal in managing the vast and complex data involved in cybersecurity. These include data on vulnerabilities, threats, and the structure of cyberattacks themselves. By enabling the automated categorization of these elements and the identification of attack patterns, graphs streamline the process of threat detection and mitigation.
One of the standout advantages of utilizing graphs in cybersecurity is the ability to visualize intricate security information. This visualization aids in the timely detection of and response to cyber incidents, allows for the use of standardized terminology, and mainstreams the processing of security data. By providing a graphical representation of network topology, graphs reveal potential vulnerabilities and the possible spread of threats within a network, thereby offering invaluable insights into complex network structures. This enhanced visibility is critical for identifying unusual patterns of network flow, pinpointing single points of failure, and facilitating effective communication among cybersecurity teams.
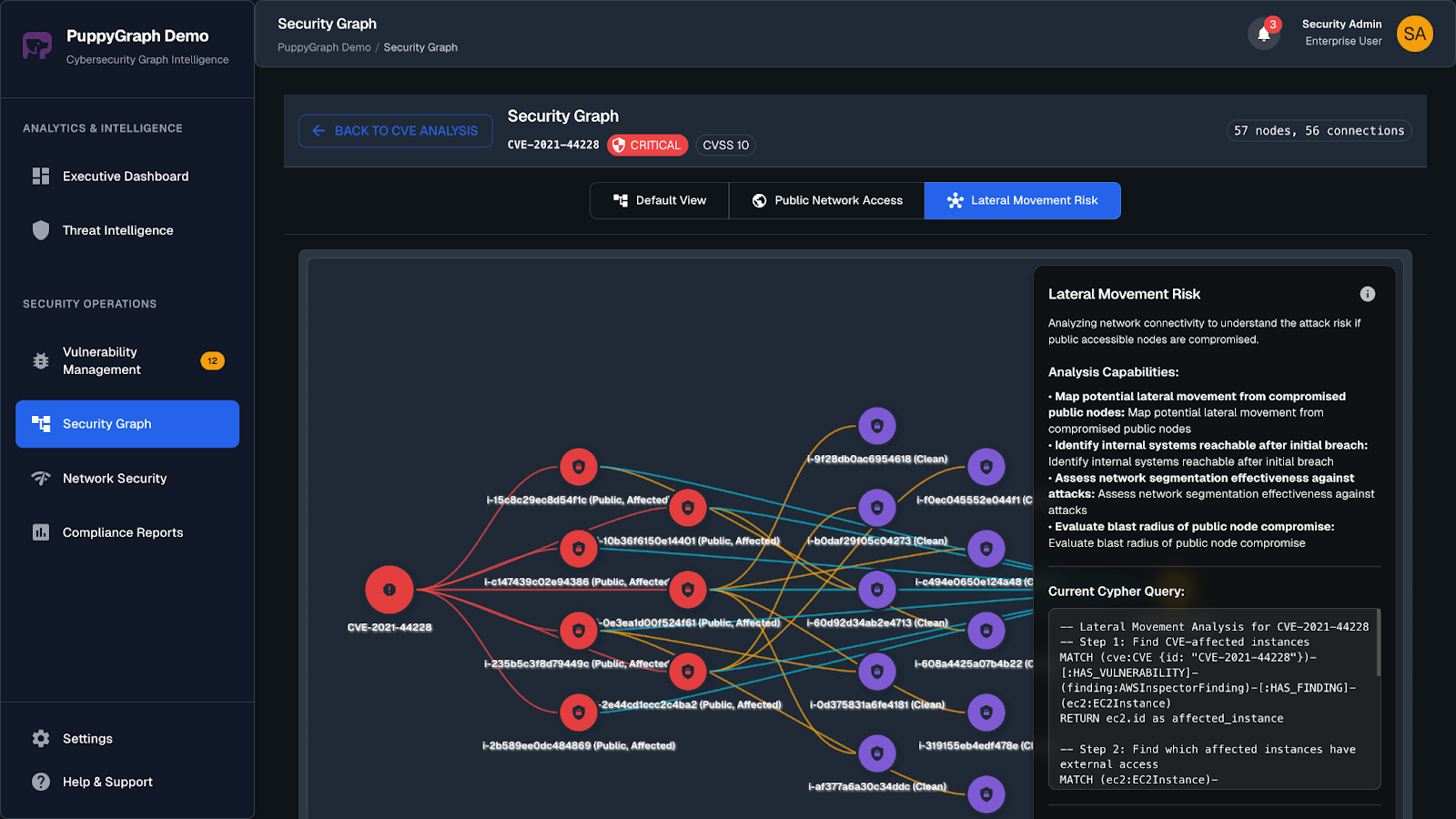
The application of graphs in cybersecurity extends beyond visualization as it encompasses the automation of threat detection and mitigation processes. By integrating various data sources into a cohesive graph-based model, cybersecurity systems can automate the categorization and analysis of threats. This automation not only speeds up the response to cyber incidents but also enhances the accuracy and efficiency of threat detection and mitigation.
The traditional reliance on linear data structures such as lists of alerts and logs often hinders defenders' ability to gain a comprehensive view of their systems, leading to critical blind spots. In contrast, attackers exploit the network's interconnectedness, viewing it as a graph to identify and leverage vulnerabilities. By adopting a similar graph-based perspective, defenders can significantly enhance their security posture. A complete graph of an organization’s infrastructure, or a digital twin, provides a holistic and continuously updated model of the entire network, enabling the identification of valuable assets, the generation of targeted alerts, and the analysis of identity and access management policies.
Fundamentals of Cybersecurity Graphs
Cybersecurity graphs are crucial for understanding and navigating the complex landscape of cybersecurity threats and defenses. They primarily consist of two foundational elements: knowledge graphs and graph databases. Cybersecurity knowledge graphs (CKGs) organize and depict the relationships between different cybersecurity entities and concepts. By utilizing semantic networks and ontologies, CKGs connect nodes (representing objects and concepts) with edges (depicting relationships) to form a vast, interconnected network of cybersecurity knowledge. This structure enables a deeper understanding and more effective analysis of cybersecurity threats, making CKGs invaluable for both offensive and defensive cybersecurity strategies in dynamic environments.

For handling Cybersecurity Knowledge Graphs, graph databases are undoubtedly the preferred option. These databases, organized around nodes (vertices) and relationships (edges), form a network of interlinked data showcasing the interactions among different entities. Unlike traditional relational databases, graph databases excel in cybersecurity applications because of their adeptness at mapping and analyzing sequences of actions, which are common characteristics of cyber attacks. They leverage powerful graph algorithms, such as Breadth-First Search (BFS), Depth-First Search (DFS), and Dijkstra’s algorithm, to navigate the data network and identify patterns indicative of malicious activities. This capability significantly enhances the detection of threats and vulnerabilities, contributing to more robust data protection and operational safety.
Together, knowledge graphs and graph databases form the backbone of cybersecurity graphs, each playing a pivotal role in the fight against cyber threats. While knowledge graphs provide a structured and comprehensive understanding of cybersecurity knowledge, graph databases offer the technical means to efficiently manage and analyze data related to cyber threats.
Techniques for Cybersecurity Analysis Using Graphs
Building on the foundational concepts above, the application of graph-based analysis techniques leverages the inherent strengths of knowledge graphs and graph databases, offering a multi-faceted approach to enhancing cybersecurity measures. Through structured data representation, predictive analytics, and insightful visualizations, these techniques extend the core concepts of cybersecurity graphs into practical, impactful cybersecurity strategies.
Knowledge graph-based models are pivotal in the realm of cybersecurity, offering diverse approaches tailored to meet specific analysis needs. These models excel in various applications, from depicting intricate network infrastructures to detailed cyber-threat intelligence and conceptual frameworks of cybersecurity properties. By facilitating the organization and accessibility of vast amounts of cybersecurity data, these models significantly enhance cyber-situational awareness and bolster cyber-resilience strategies. The structured representation they provide allows for a more systematic approach to threat analysis and defense planning, making critical information readily available and actionable for security professionals.
Visualization techniques in graph-based cybersecurity analysis serve as powerful tools for interpreting complex data. By converting intricate cybersecurity information into more comprehensible visual formats, these techniques facilitate a deeper understanding of the data at hand. Visualization supports the exploration of log data, vulnerabilities, attack patterns, and intrusion detection efforts, providing security analysts with clear and insightful views of the cybersecurity landscape. This clarity is essential for the efficient detection and mitigation of threats, enabling analysts to quickly identify and address potential vulnerabilities.
The application of machine learning in cybersecurity graphs marks a significant advancement in threat detection and response. Through the analysis of the interconnected data in knowledge graphs and graph databases, machine learning algorithms can uncover anomalies and predict potential threats with high accuracy. This predictive capability enables the proactive identification and mitigation of cyber threats, leveraging automated reasoning to infer new threats or vulnerabilities from existing data patterns. The dynamic nature of these techniques allows for real-time threat intelligence and adaptive cybersecurity measures, ensuring that defenses evolve in step with emerging threats.

Challenges and Considerations
The adoption of graph-based approaches in cybersecurity also introduces several challenges and considerations that must be addressed to effectively leverage this technology.
Data Complexity and Volume
One of the primary challenges in using graphs for cybersecurity is managing the complexity and volume of data. Cybersecurity environments generate vast amounts of data from various sources, including network traffic, logs, and threat intelligence feeds. Modeling this data as graphs can quickly lead to large, complex structures that are difficult to analyze and interpret. The challenge is further compounded by the dynamic nature of cyber threats, requiring continuous updates to the graph as new data arrives.
Performance and Scalability
Related to the challenge of data complexity is the issue of performance and scalability. Effective cybersecurity analysis requires real-time or near-real-time processing of data to detect and respond to threats promptly. Graph databases and analytics platforms must be capable of handling high-throughput data ingestion, complex queries, and large-scale graph computations without significant performance degradation. This necessitates advanced database architectures, efficient graph algorithms, and scalable infrastructure.
Data Integration and Fusion
Cybersecurity data comes from diverse sources, each with its own format, semantics, and level of granularity. Integrating this data into a coherent graph model poses significant challenges. It requires effective data fusion techniques to combine heterogeneous data while preserving its semantic relationships. Additionally, cybersecurity analysts must deal with incomplete or inaccurate data, further complicating the integration process.
Security and Privacy
The use of graphs in cybersecurity raises important security and privacy considerations. Graphs often contain sensitive information about network configurations, vulnerabilities, and user activities. Protecting this information from unauthorized access or disclosure is paramount. Graph databases and analytics platforms must implement robust security measures, including access controls, encryption, and privacy-preserving techniques, to safeguard data.
Interpretability and Usability
Another challenge is ensuring the interpretability and usability of graph-based cybersecurity tools. Graphs can provide deep insights into cyber threats, but only if they are accessible to analysts. This requires intuitive visualization tools, user-friendly query languages, and effective summarization techniques to help analysts navigate and make sense of complex graph data. Additionally, there is a need for training and education to equip cybersecurity professionals with the skills to effectively use graph-based tools.
Best Practices for Cybersecurity Graph Implementations
To maximize the effectiveness of graph-based cybersecurity solutions, organizations must adhere to best practices that ensure the integrity, performance, and usability of these systems. Here are some key best practices for cybersecurity graph implementations:
Define Clear Objectives
Before implementing a graph-based solution, clearly define what you aim to achieve. Whether it's identifying attack patterns, enhancing threat intelligence, or improving incident response, having clear objectives guides the design and deployment of your graph database.
Ensure Data Quality and Integration
Graphs are only as good as the data they contain. Ensure high-quality, accurate data by implementing robust data validation and cleansing processes. Integrate data from diverse sources, such as logs, alerts, and threat intelligence feeds, to create a comprehensive view of your cybersecurity landscape. Utilize graph algorithms to automate the detection of malicious patterns and activities, replacing the need for manually written correlation rules.
Adopt a Scalable Graph Analytic Tool
Choose a graph analytic tool that can scale with your data volume and complexity. Graph databases, such as Neo4j and AWS Neptune, are commonly considered for their capabilities to navigate and manage large, intricate data structures that are fundamental to cybersecurity.
Given that graph databases in cybersecurity contain sensitive information, implementing robust security measures is crucial. This includes access controls, encryption, and monitoring to prevent unauthorized access or data breaches. Additionally, consider privacy-preserving techniques to protect individual privacy while analyzing graph data.
Build Cybersecurity Graphs With PuppyGraph
If one doesn't have the resources to build and manage the complex ETL process, the graph analytic engine PuppyGraph is better at integrating into cybersecurity contexts, thanks to its proficiency and scalability in handling complex, large-scale data architectures. These databases or engines should support high-throughput data ingestion and complex queries without significant performance degradation.
PuppyGraph sets itself apart by decoupling storage from computation, capitalizing on the advantages of columnar data lakes to deliver significant scalability and performance gains. When conducting intricate graph queries like multi-hop neighbor searches, the need arises to join and manipulate numerous records. The columnar approach to data storage enhances read efficiency, allowing for the quick fetching of only the relevant columns needed for a query, thus avoiding the exhaustive scanning of entire rows.

With PuppyGraph, you can use the SQL data stores as you normally would, while reaping the benefits of graph-specific use cases such as complex pattern matching and efficient pathfinding. It avoids the additional complexity and resource consumption of maintaining a separate graph database and the associated ETL pipelines.

Utilize Advanced Graph Algorithms
Leverage advanced graph algorithms for community detection, anomaly detection, and pattern recognition to identify potential threats and vulnerabilities within your network. These algorithms can automate the identification of malicious activities, significantly reducing the time and effort required for manual analysis.
Continuous Monitoring and Updating
The cyber threat landscape is constantly evolving. Continuously monitor your graph-based systems for new threats and update your graph models and algorithms accordingly. This includes updating the graph with new data sources, refining algorithms based on emerging threat patterns, and adjusting security measures to counter new vulnerabilities.
Conclusion
In conclusion, the intersection of graphs and cybersecurity opens up new avenues for safeguarding digital assets. Graphs provide an exceptional framework for visualizing and analyzing the intricate relationships and patterns inherent in cybersecurity data. Graphs are poised to play a pivotal role in our defense arsenal, signifying a dynamic shift towards more innovative and effective cybersecurity measures.
Ready to add cybersecurity graphs on your existing SQL data? Download the forever free PuppyGraph Developer Edition or begin your free 30-day trial of the Enterprise Edition today.
Get started with PuppyGraph!
Developer Edition
- Forever free
- Single noded
- Designed for proving your ideas
- Available via Docker install
Enterprise Edition
- 30-day free trial with full features
- Everything in developer edition & enterprise features
- Designed for production
- Available via AWS AMI & Docker install






